“I wonder if it is possible to hand out a static route to a user, when a VPN is established?”
So this admin found his user object, tabbed to Dial-in, enabled Apply Static Routes and clicked Static Routes. Added the wanted route and saved it all. Next, the user reconnected the VPN – and things started to go wrong…
After messing things back to normal, I – sorry, the admin - began reading the help text –
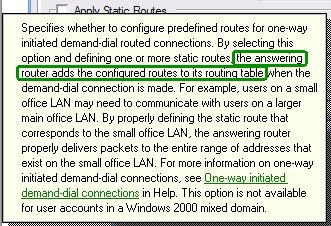
Hmmm, the answering server – the ISA server in this case – does this. It is not handed to the client. Bad luck!
The worse part of this – and the reason I’m writing this – is to warn you. If you grant you helpdesk, decentral admins etc. the permissions to change these settings on your user objects having VPN access, you risk they make your ISA server unavailable!
The GUI settings corresponds to these LDAP properties –
1> msRADIUSFramedRoute: 8.8.8.0/24 0.0.0.0 1;
1> msRASSavedFramedRoute: 8.8.8.0/24 0.0.0.0 1;
So if someone has change access to these properties – i.e. they have full permissions on the user, explicit permissions for the properties or implicit permissions you are at risk. Beware that the RAS-Information a.k.a “Remote Access Information” property set includes these properties. Note that the default for Active Directory is to give the built-in Account Operators group permissions to update these.
No comments:
Post a Comment