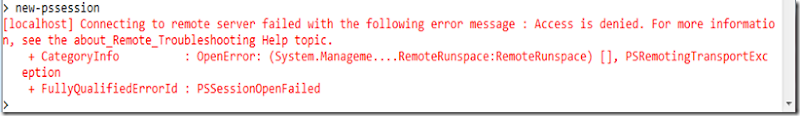
One of the great features of PowerShell V2 is the remote session support. But in the default configuration only local administrators can create a remote session. This is what a normal user sees -
This is how you delegate the feature to other users – the easy way.
First, create a local group and insert the user(s)
net localgroup "PowerShell Session Users" /add
net localgroup "PowerShell Session Users" the-user /add
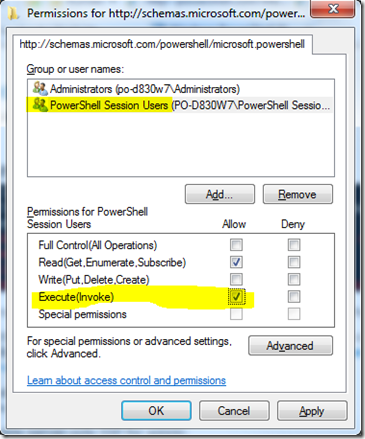
Second, execute this command to bring up the permissions GUI
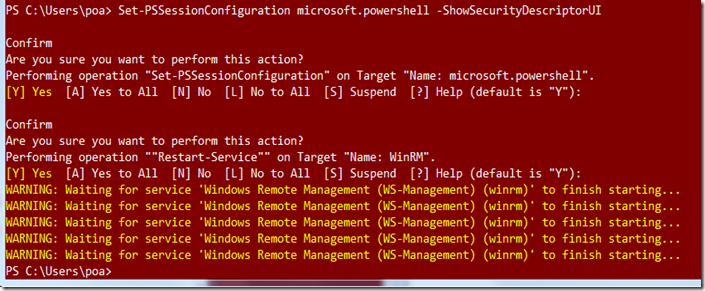
Set-PSSessionConfiguration microsoft.powershell -ShowSecurityDescriptorUI
add the group and grant execute (invoke) permissions -
Note that you have to restart the service -
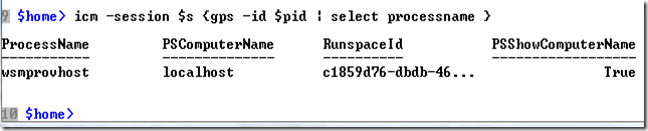
And finally, try it out.
Let me draw your attention to two things in the picture above. First, the remote command is executed by a wsmprovhost process and second, extra properties are returned even though only the processname was selected. The extra properties are useful if you execute command on multiple sessions. In this way, you can recognize the returned objects.